Q: 11
Refer to the information below to answer the question.
During the investigation of a security incident, it is determined that an unauthorized individual
accessed a system which hosts a database containing financial information.
Aside from the potential records which may have been viewed, which of the following should be the
PRIMARY concern regarding the database information?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
DRAG DROP Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media. 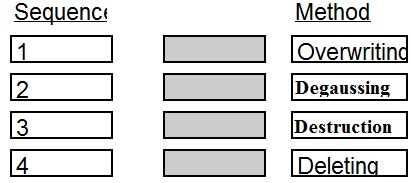
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
An organization is considering outsourcing applications and data to a Cloud Service
Provider (CSP). Which of the following is the MOST important concern regarding
privacy?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
An advantage of link encryption in a communications network is that it
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
DRAG DROP Place the following information classification steps in sequential order. 
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
DRAG DROP A software security engineer is developing a black box-based test plan that will measure the system's reaction to incorrect or illegal inputs or unexpected operational errors and situations. Match the functional testing techniques on the left with the correct input parameters on the right. 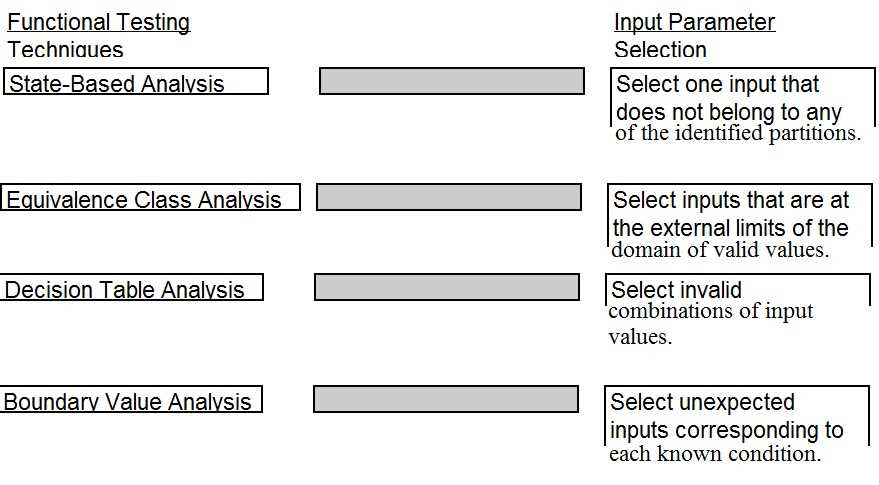
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 17
DRAG DROP In which order, from MOST to LEAST impacted, does user awareness training reduce the occurrence of the events below? 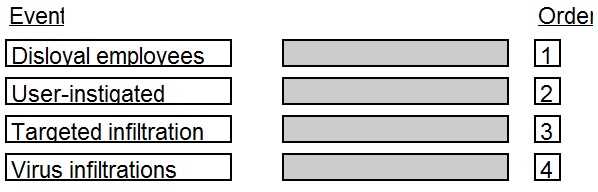
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
DRAG DROP Order the below steps to create an effective vulnerability management process. 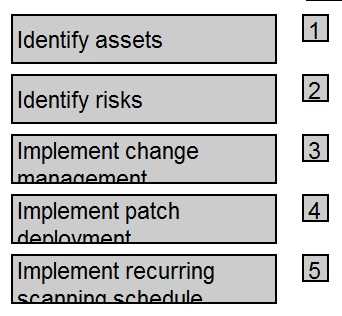
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
Which of the following is the MOST effective attack against cryptographic hardware modules?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 20
Which of the following is a security weakness in the evaluation of common criteria (CC) products?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 10

