DRAG DROP Match the name of access control model with its associated restriction. Drag each access control model to its appropriate restriction access on the right. 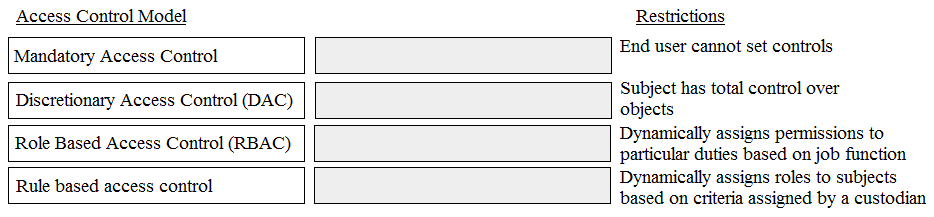
Q: 1
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Which of the following value comparisons MOST accurately reflects the agile development
approach?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
A security consultant has been hired by a company to establish its vulnerability management
program. The consultant is now in the deployment phase. Which of the following tasks is part of this
process?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
When in the Software Development Life Cycle (SDLC) MUST software security functional
requirements be defined?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
What does the result of Cost-Benefit Analysis (C8A) on new security initiatives provide?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
A company whose Information Technology (IT) services are being delivered from a Tier 4 data center,
is preparing a companywide Business Continuity Planning (BCP). Which of the following failures
should the IT manager be concerned with?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
HOTSPOT In the network design below, where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point (WAP) that provides contractors access to the Internet and authorized enterprise services? 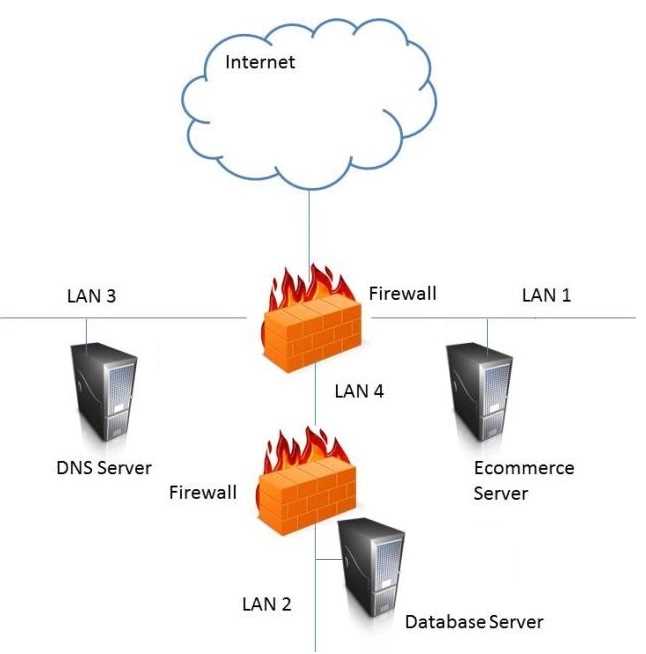
Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
DRAG DROP Rank the Hypertext Transfer protocol (HTTP) authentication types shows below in order of relative strength. Drag the authentication type on the correct positions on the right according to strength from weakest to strongest. 
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Which of the following management process allows ONLY those services required for users to
accomplish
their tasks, change default user passwords, and set servers to retrieve antivirus updates?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 10
DRAG DROP Match the name of access control model with its associated restriction. Drag each access control model to its appropriate restriction access on the right. 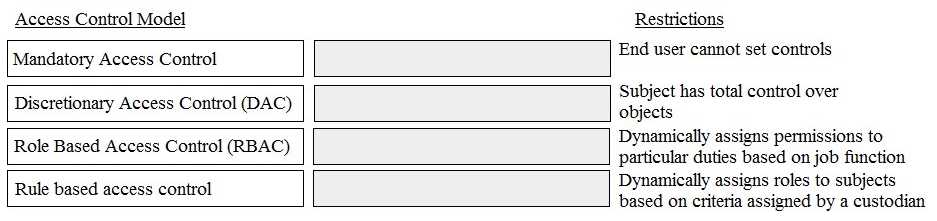
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 10

