SC-900.pdf
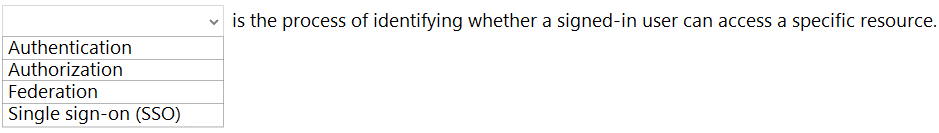
HOTSPOT Select the answer that correctly completes the sentence. 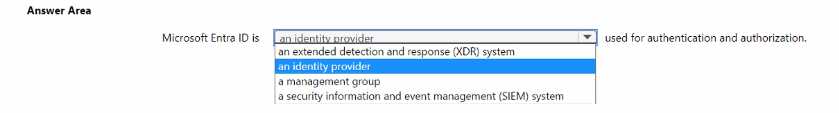
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. 
HOTSPOT Select the answer that correctly completes the sentence. 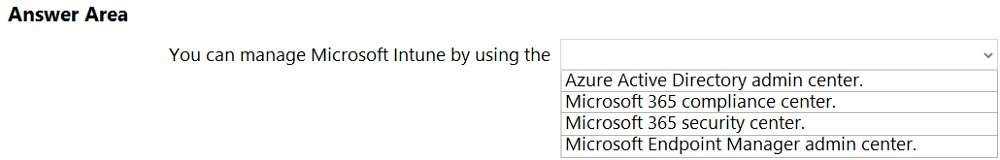
HOTSPOT Select the answer that correctly completes the sentence. 
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. 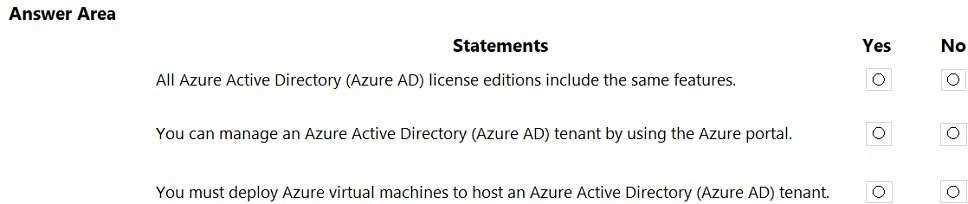
HOTSPOT Select the answer that correctly completes the sentence. 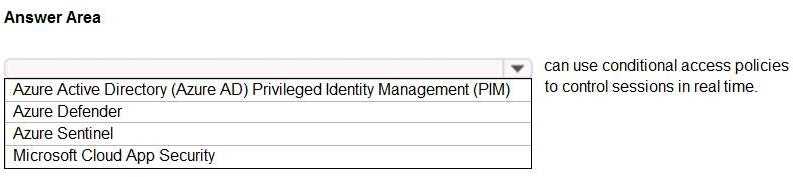
HOTSPOT Select the answer that correctly completes the sentence. 
HOTSPOT Select the answer that correctly completes the sentence. 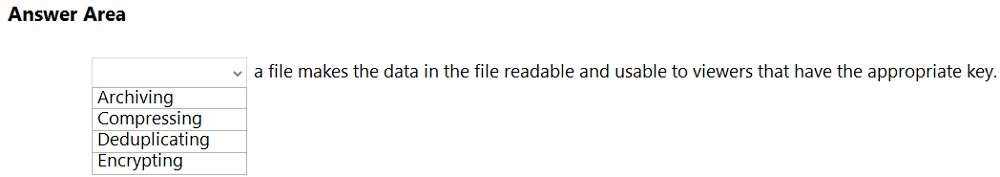
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. 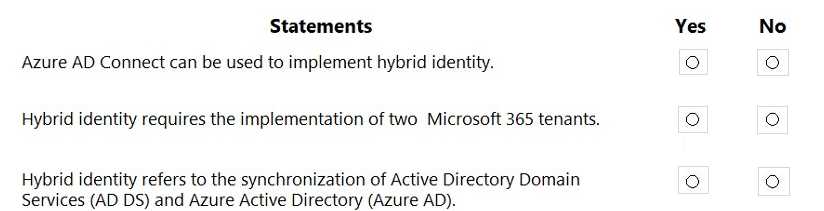
HOTSPOT Select the answer that correctly completes the sentence.