SC-300.pdf
Your network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table. 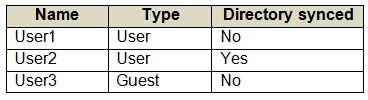 All the users work remotely. Azure AD Connect is configured in Azure AD as shown in the following exhibit.
All the users work remotely. Azure AD Connect is configured in Azure AD as shown in the following exhibit. 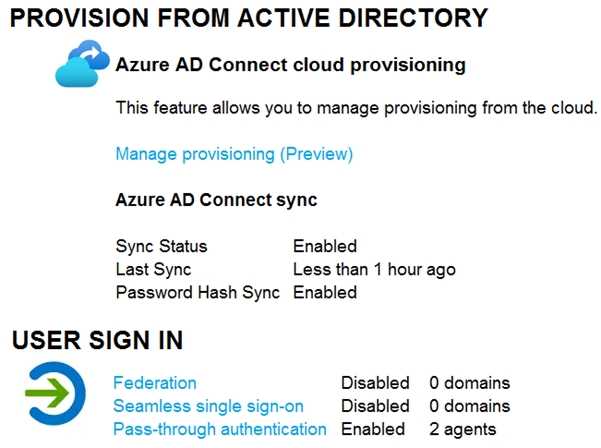 Connectivity from the on-premises domain to the internet is lost. Which users can sign in to Azure AD?
Connectivity from the on-premises domain to the internet is lost. Which users can sign in to Azure AD?
You have an Azure AD tenant named contoso.com that contains the resources shown in the following table. You create a user named Admin 1.  You need to ensure that Admin can enable Security defaults for contoso.com. What should you do first?
You need to ensure that Admin can enable Security defaults for contoso.com. What should you do first?
You have a Microsoft 365 tenant. You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click theExhibittab.) 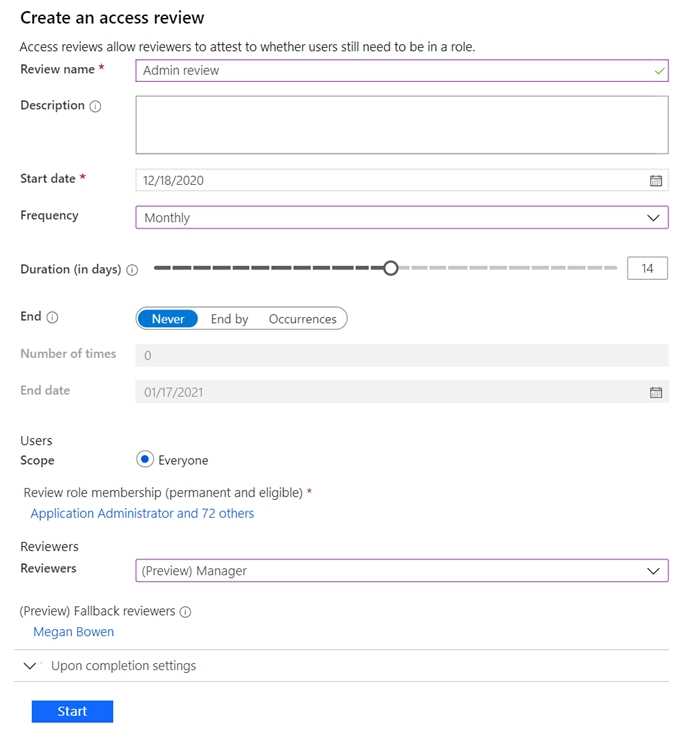 You discover that all access review requests are received by Megan Bowen. You need to ensure that the manager of each department receives the access reviews of their respective department. Solution: You modify the properties of the IT administrator user accounts. Does this meet the goal?
You discover that all access review requests are received by Megan Bowen. You need to ensure that the manager of each department receives the access reviews of their respective department. Solution: You modify the properties of the IT administrator user accounts. Does this meet the goal?

