AZ 104 Latest
DRAG DROP - You have an Azure subscription that contains two virtual networks named VNet1 and VNet2. Virtual machines connect to the virtual networks. The virtual networks have the address spaces and the subnets configured as shown in the following table. 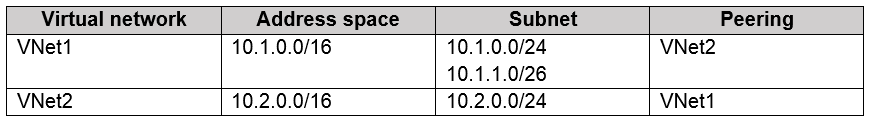 You need to add the address space of 10.33.0.0/16 to VNet1. The solution must ensure that the hosts on VNet1 and VNet2 can communicate. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You need to add the address space of 10.33.0.0/16 to VNet1. The solution must ensure that the hosts on VNet1 and VNet2 can communicate. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place: 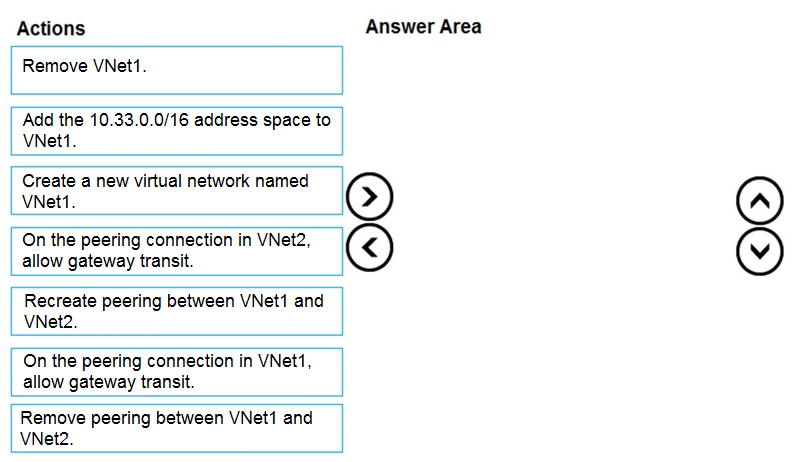
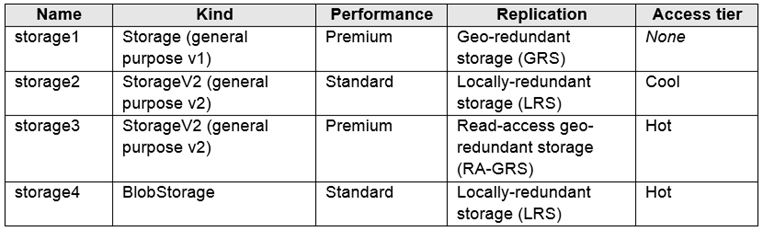 You need to identify which storage account can be converted to zone-redundant storage
(ZRS) replication by requesting a live migration from Azure support. What should you
identify?
You need to identify which storage account can be converted to zone-redundant storage
(ZRS) replication by requesting a live migration from Azure support. What should you
identify? Which cmdlet should you run to deploy the template?
Which cmdlet should you run to deploy the template?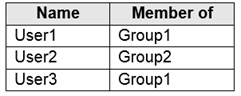 You plan to monitor storage1 and to configure email notifications for the signals shown in
the following table.
You plan to monitor storage1 and to configure email notifications for the signals shown in
the following table.
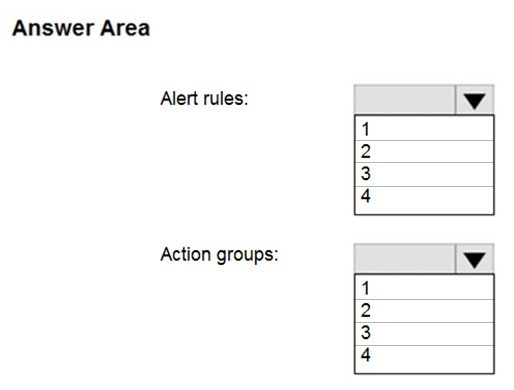
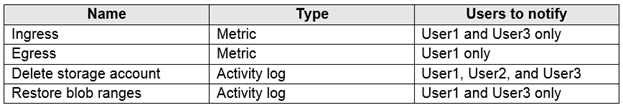 You need to identify the minimum number of alert rules and action groups required for the
planned monitoring.
How many alert rules and action groups should you identify? To answer, select the
appropriate options in the answer area.
Hot Area:
You need to identify the minimum number of alert rules and action groups required for the
planned monitoring.
How many alert rules and action groups should you identify? To answer, select the
appropriate options in the answer area.
Hot Area:
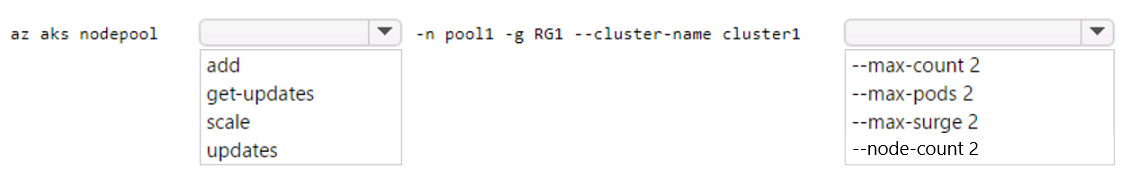
DRAG DROP - You onboard 10 Azure virtual machines to Azure Automation State Configuration. You need to use Azure Automation State Configuration to manage the ongoing consistency of the virtual machine configurations. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select. Select and Place: 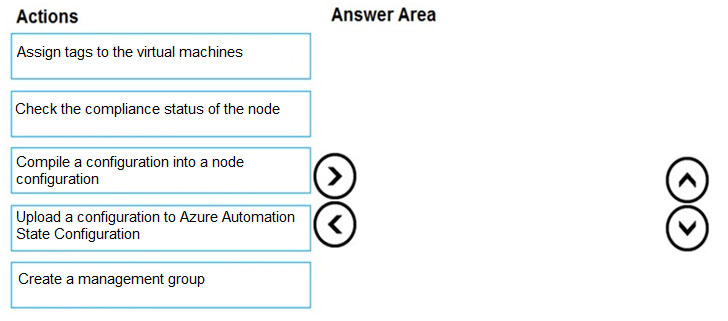
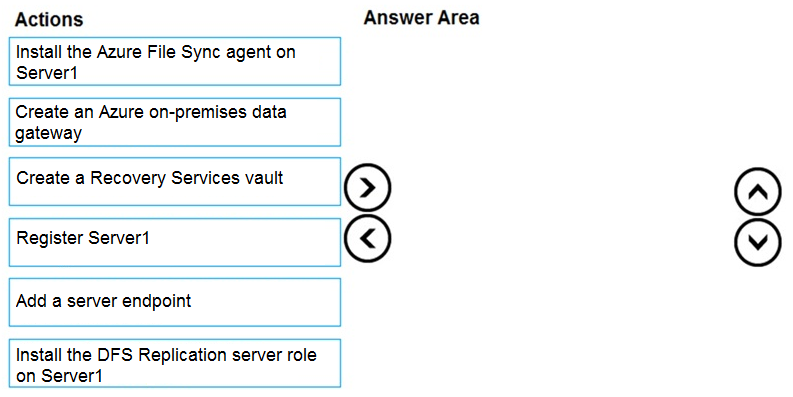
DRAG DROP - You have an on-premises file server named Server1 that runs Windows Server 2016. You have an Azure subscription that contains an Azure file share. You deploy an Azure File Sync Storage Sync Service, and you create a sync group. You need to synchronize files from Server1 to Azure. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place: