CISCO 200-201
Q: 1
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Options
Q: 2
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same
key?
Options
Q: 3
Which step in the incident response process researches an attacking host through logs in a SIEM?
Options
Q: 4
Which security monitoring data type requires the largest storage space?
Options
Q: 5
Which security technology allows only a set of pre-approved applications to run on a system?
Options
Q: 6
What makes HTTPS traffic difficult to monitor?
Options
Q: 7
Refer to the exhibit.
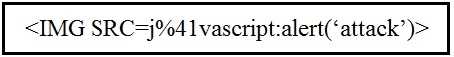 Which kind of attack method is depicted in this string?
Which kind of attack method is depicted in this string?
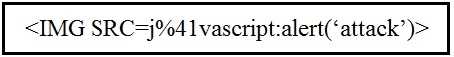 Which kind of attack method is depicted in this string?
Which kind of attack method is depicted in this string?Options
Q: 8
Refer to the exhibit.
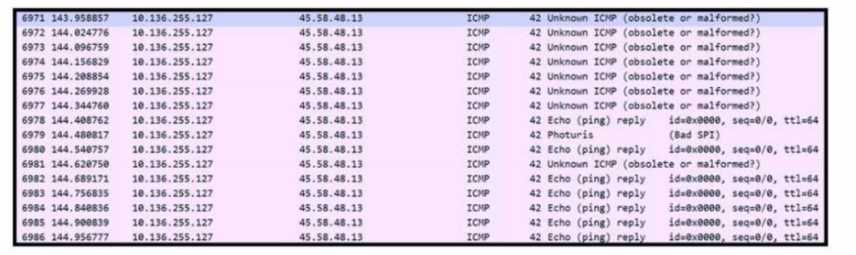 Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?
 Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is
occurring?Options
Q: 9
Refer to the exhibit.
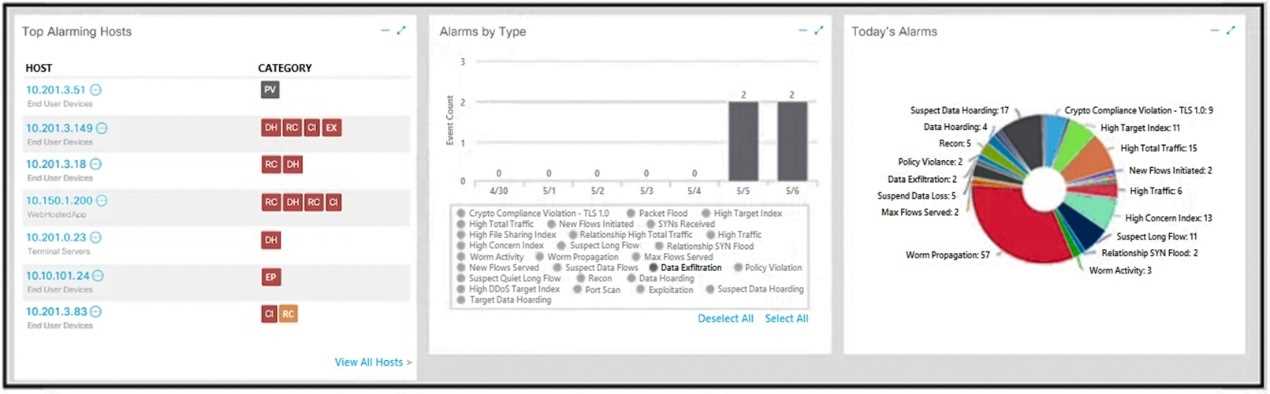 What is the potential threat identified in this Stealthwatch dashboard?
What is the potential threat identified in this Stealthwatch dashboard?
 What is the potential threat identified in this Stealthwatch dashboard?
What is the potential threat identified in this Stealthwatch dashboard?Options
Q: 10
Refer to the exhibit.
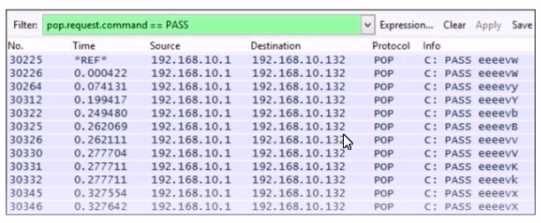 Which alert is identified from this packet capture?
Which alert is identified from this packet capture?
 Which alert is identified from this packet capture?
Which alert is identified from this packet capture?Options
Question 1 of 10

